
Automated User Tracking with the Cookiebot Solution

Automated User Tracking with the Cookiebot Solution
What Is Identity Proofing and Why It’s Only Part of the Solution
October 12, 2022

When the COVID-19 pandemic led to widespread lockdowns, it accelerated a trend that had been transforming business for decades: the shift of services from in-person to online. As more and more consumers turned to the web to conduct business using various devices, identity proofing in the process of fraud prevention became increasingly critical. In 2021 alone, more than 2.8 million fraud reports were filed with the FTC, and bank transactions accounted for the highest aggregate losses reported ($756 million).
Join our webinar on November 10, 2022, to learn more about ABBYY Proof of Identity.
At the same time, consumer trust has become a critical factor in building brand loyalty and customer retention, particularly in industries that require handling sensitive information. In a 2021 survey , 38.8 percent of consumers with higher-than-average levels of digital trust said they would open their next account with their current bank, compared to just 21.3 percent of respondents with lower-than-average trust levels.
One of the critical aspects of online services involving sensitive data—such as banking, healthcare, and government—is identity proofing, using uploaded documents to verify a user’s identity. This requires not only intake of identifying documents (such as a driver’s license) but also verifying the validity of these documents and confirming that they reflect the user’s identity. Gartner predicts that by 2023,85 percent of organizations will be using document-centric identity proofing as part of their onboarding processes.
What is identity proofing?
Identity proofing is the process of confirming that a user is who they say they are. Accomplishing this requires matching a user’s _claimed identity_—what the National Institute of Standards and Technology (NIST) defines as “an applicant’s declaration of unvalidated and unverified personal attributes”— with their actual identity, as proven by data and documentation.
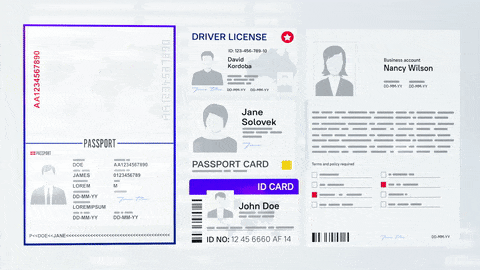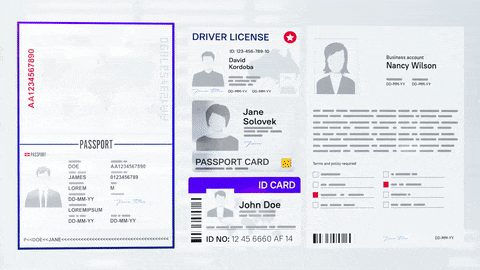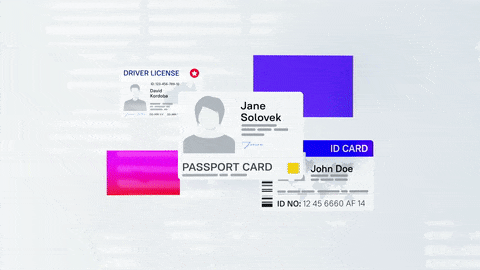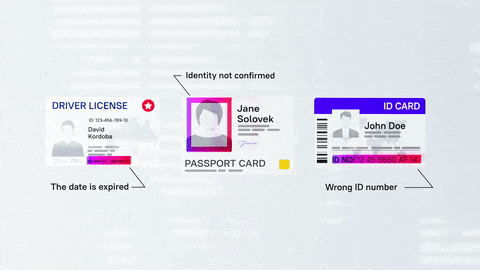
A common misperception of identity proofing equates it with another common online security concept, identity authentication. Authentication is the use of a combination of credentials—generally a username and password—to gain access to a resource. However, before users can be assigned credentials, especially for access to sensitive resources, they must first verify who they are through identity proofing.
How does identity proofing work?
The NIST identifies three steps that make up the identity proofing process :
- Resolution: Collect the individual’s personal information (name, address, date of birth, etc.) and identity evidence (such as a passport or driver’s license).
- Validation: Determine the authenticity, validity, and accuracy of the information and documentation provided.
- Verification: Confirm and establish a link between the claimed identity and the actual identity of the subject presenting the evidence.
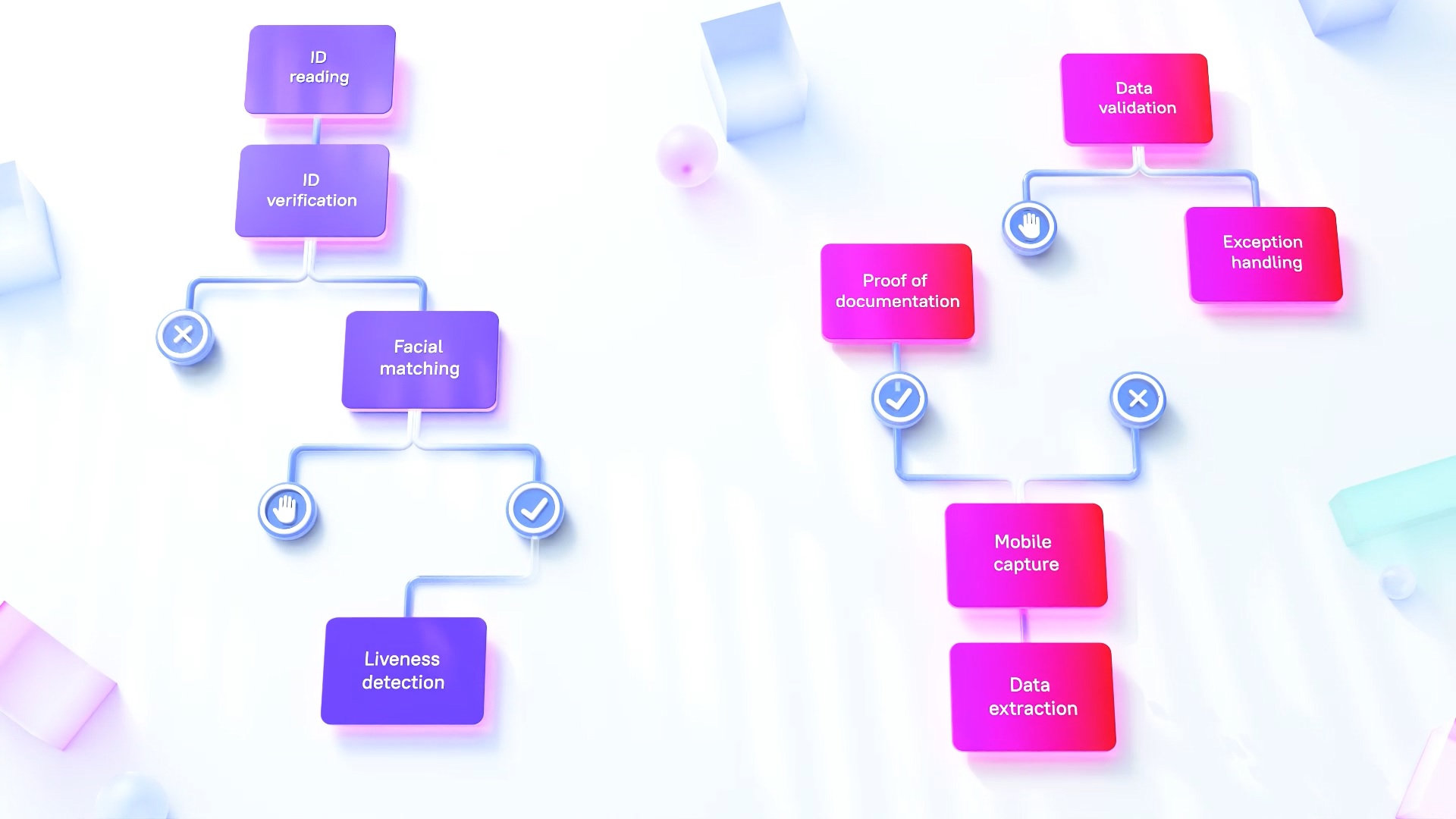
Manual approaches to this detailed process can be time-consuming, tedious, and at high risk for error. Fortunately, today’s identity proofing systems can leverage automation and AI to carry out each step without the need for human intervention in most cases.
What’s the difference between identity proofing and identity affirmation … and why do we need both?
While identity proofing is a vital capability for organizations looking to secure their processes, there is more to the story. Sophisticated scammers are capable of creating realistic documentation that may even trick some verification systems, even though the human being they describe is purely fictional. This is why businesses need identity affirmation alongside traditional identity proofing.
Identity affirmation, according to Gartner , “describes capabilities that either assess solely whether the real-world identity exists or can provide supporting risk or trust signals to an identity claim.” Successful identity affirmation requires access to multiple outside data sources. For example, in a low-confidence, high-risk transaction, a business will want to verify an address via a utility bill, birth certificate, income statement, and credit bureau data to verify that this data corresponds to an actual human being.
When businesses leverage identity proofing and identity affirmation in tandem, they can enjoy a high level of confidence that the users they interact with really are who they say they are.
Is there a “one-stop shop” for identity proofing and affirmation capabilities?
While many vendors offer identity proofing and affirmation tools, few actually deliver the full slate of required functions. When ABBYY developers designed our solution, we made sure to include a full slate of capabilities for you, including
- ID reading, including mobile capture and document classification
- ID verification, including image-tampering fraud detection
- Facial matching based on a top-rated NIST-rated algorithm with extremely low bias
- Trailing documents (document-centric identity affirmation)
- Exception handling (optional human auditing of certain transactions)
- Process intelligence and mining to identify opportunities for process improvement
What are common use cases for identity proofing?
While fraud can happen in nearly any industry, sectors with a high frequency of high-risk transactions stand to derive the greatest benefit from AI-driven identity proofing solutions. Here’s a brief sampling of how businesses in various industries are putting identity proofing to use:
Banking and financial services
- Anti-Money Laundering (AML) and Know Your Customer (KYC) regulation compliance
- Customer onboarding and new account opening
- Loan and mortgage applications
Healthcare
- Confirming patient identity for HIPAA requirements
- Distributing prescription medications
Insurance
- Claims processing
Telecom
- Point-of-sale verification to avoid subscription fraud
Government
- New driver’s license/ID applications
- License/ID renewals
- Title-related services
- Compliance with Real ID requirements
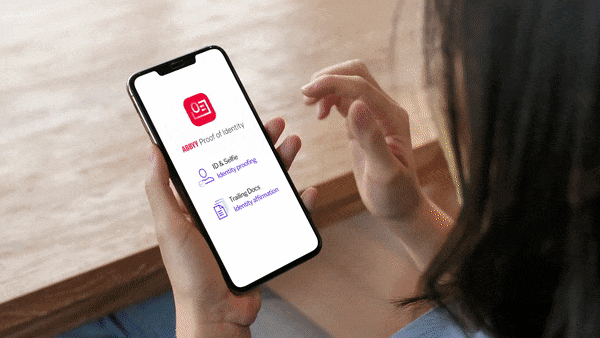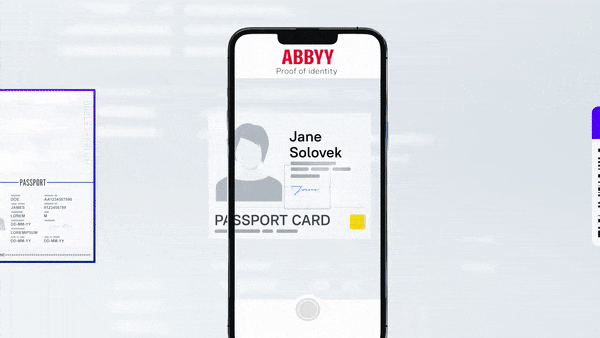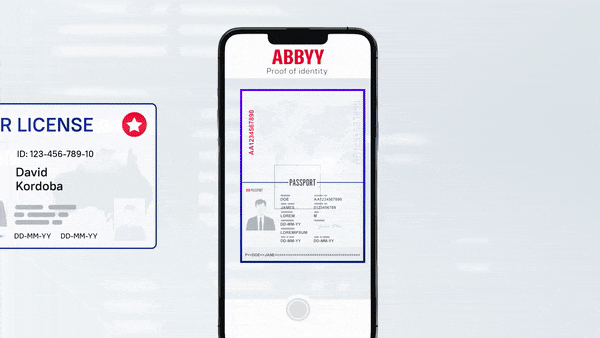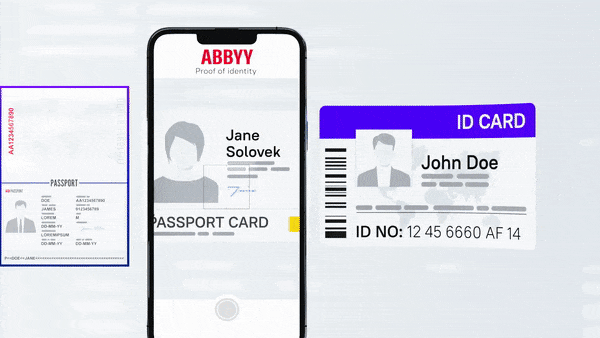
Over the course of just a few years, the volume and complexity of online transactions has grown exponentially, both for better and for worse. Fortunately, identity proofing and affirmation solutions can help businesses continue to meet consumers’ demands for efficient, convenient services while also staying one step ahead of fraudulent actors.
Not only can you minimize the risk of fraud—and the corresponding costs in terms of money and reputation—but you can also earn and build upon the trust of your customers, building relationships that can support business goals for years to come.
Learn about ABBYY’s comprehensive identity proofing solution. ABBYY Proof of Identity does it all.
ABBYY Proof of Identity
Easy for your customers. Secure for your business.
Artificial Intelligence (AI) Customer Experience Customer Onboarding Data Privacy Digital Transformation Enterprise Financial Services Government Healthcare Intelligent Automation Intelligent Document Processing (IDP) Insurance Legal Mobile Robotic Process Automation (RPA) Transportation & Logistics
Like, share or repost
Share
Subscribe for blog updates
First name*
E-mail*
Сountry*
СountryAfghanistanAland IslandsAlbaniaAlgeriaAmerican SamoaAndorraAngolaAnguillaAntarcticaAntigua and BarbudaArgentinaArmeniaArubaAustraliaAustriaAzerbaijanBahamasBahrainBangladeshBarbadosBelgiumBelizeBeninBermudaBhutanBoliviaBonaire, Sint Eustatius and SabaBosnia and HerzegovinaBotswanaBouvet IslandBrazilBritish Indian Ocean TerritoryBritish Virgin IslandsBrunei DarussalamBulgariaBurkina FasoBurundiCambodiaCameroonCanadaCape VerdeCayman IslandsCentral African RepublicChadChileChinaChristmas IslandCocos (Keeling) IslandsColombiaComorosCongo (Brazzaville)Congo, (Kinshasa)Cook IslandsCosta RicaCroatiaCuraçaoCyprusCzech RepublicCôte d’IvoireDenmarkDjiboutiDominicaDominican RepublicEcuadorEgyptEl SalvadorEquatorial GuineaEritreaEstoniaEthiopiaFalkland Islands (Malvinas)Faroe IslandsFijiFinlandFranceFrench GuianaFrench PolynesiaFrench Southern TerritoriesGabonGambiaGeorgiaGermanyGhanaGibraltarGreeceGreenlandGrenadaGuadeloupeGuamGuatemalaGuernseyGuineaGuinea-BissauGuyanaHaitiHeard and Mcdonald IslandsHoly See (Vatican City State)HondurasHong Kong, SAR ChinaHungaryIcelandIndiaIndonesiaIraqIrelandIsle of ManIsraelITJamaicaJapanJerseyJordanKazakhstanKenyaKiribatiKorea (South)KuwaitKyrgyzstanLao PDRLatviaLebanonLesothoLiberiaLibyaLiechtensteinLithuaniaLuxembourgMacao, SAR ChinaMacedonia, Republic ofMadagascarMalawiMalaysiaMaldivesMaliMaltaMarshall IslandsMartiniqueMauritaniaMauritiusMayotteMexicoMicronesia, Federated States ofMoldovaMonacoMongoliaMontenegroMontserratMoroccoMozambiqueMyanmarNamibiaNauruNepalNetherlandsNetherlands AntillesNew CaledoniaNew ZealandNicaraguaNigerNigeriaNiueNorfolk IslandNorthern Mariana IslandsNorwayOmanPakistanPalauPalestinian TerritoryPanamaPapua New GuineaParaguayPeruPhilippinesPitcairnPolandPortugalPuerto RicoQatarRomaniaRwandaRéunionSaint HelenaSaint Kitts and NevisSaint LuciaSaint Pierre and MiquelonSaint Vincent and GrenadinesSaint-BarthélemySaint-Martin (French part)SamoaSan MarinoSao Tome and PrincipeSaudi ArabiaSenegalSerbiaSeychellesSierra LeoneSingaporeSint Maarten (Dutch part)SlovakiaSloveniaSolomon IslandsSouth AfricaSouth Georgia and the South Sandwich IslandsSouth SudanSpainSri LankaSurinameSvalbard and Jan Mayen IslandsSwazilandSwedenSwitzerlandTaiwan, Republic of ChinaTajikistanTanzania, United Republic ofThailandTimor-LesteTogoTokelauTongaTrinidad and TobagoTunisiaTurkeyTurks and Caicos IslandsTuvaluUgandaUkraineUnited Arab EmiratesUnited KingdomUnited States of AmericaUruguayUS Minor Outlying IslandsUzbekistanVanuatuVenezuela (Bolivarian Republic)Viet NamVirgin Islands, USWallis and Futuna IslandsWestern SaharaZambiaZimbabwe
I have read and agree with the Privacy policy and the Cookie policy .
I agree to receive email updates from ABBYY Solutions Ltd. such as news related to ABBYY Solutions Ltd. products and technologies, invitations to events and webinars, and information about whitepapers and content related to ABBYY Solutions Ltd. products and services.
I am aware that my consent could be revoked at any time by clicking the unsubscribe link inside any email received from ABBYY Solutions Ltd. or via ABBYY Data Subject Access Rights Form .
Referrer
Last name
Query string
Product Interest Temp
UTM Campaign Name
UTM Medium
UTM Source
ITM Source
GA Client ID
UTM Content
GDPR Consent Note
Captcha Score
Page URL
Connect with us
Also read:
- [New] In 2024, Reverberation Artisan Collection
- [Updated] In 2024, Getting Live on Instagram A Simple How-To
- [Updated] The Art of Crafting Engaging IGTV Titles for 2024
- 4 Effective Strategies to Resolve Unsupported Video File Formats
- 高品質な無料動画に上級エフェクトを加えるプロのテクニック
- 最新!動画化のためのGIFを効率よく変換するフリーソフト&サイトベスト10選
- Beginner's Journey to Mastery: How to Select and Use Effective PC Screenshots Software
- Comprehensive Guide to Breaking Encrypted ISO Images with Dependable Decoding Software
- Conversione Libera Da WMV a MP4, Preservando Il 98% Della Qualità Originale
- Easy Tutorial on Transforming TiVo Files Into High-Quality MP4 Videos
- Effortless Conversion Guide: From WMV to H.264 And Back
- Elevate Your Downloads: A Complete Guide to Setting Up Advanced Download Manager on All Platforms
- How to Convert Media Files for Optimal Playback on Smartphones Including Nokia, Samsung, HTC & Blackberry Models
- How to Efficiently Manage and Edit Your iPhone Photographs: Common Issues and Fixes
- How to Screen Mirroring Oppo K11x? | Dr.fone
- In 2024, Mac Tools to Tighten Instagram Video Content
- In 2024, Unveiling the Secrets of Lightroom on Android Platforms
- Master Seamless Audio Transition with These Six Fixes: Making Your AirPods Smartly Switch Between Apple Gadgets
- Reset Password Quickly Regaining Access Post-Hack
- Title: Automated User Tracking with the Cookiebot Solution
- Author: John
- Created at : 2024-10-08 01:28:57
- Updated at : 2024-10-15 00:27:29
- Link: https://solve-hot.techidaily.com/automated-user-tracking-with-the-cookiebot-solution/
- License: This work is licensed under CC BY-NC-SA 4.0.